Data encryption is a way to safeguard personal or sensitive information like credit card details, backup phone numbers, personal identification numbers etc. that are stored in your CRM database. It prevents the data from being stolen or lost by converting the plain (or readable) text into cypher (or non-readable) text that is accessible only to authorized parties. Even if a potential hacker gets a hold of the data, the information stored in the cypher text is non-readable.
In Zoho CRM you can encrypt custom fields using AES. Encrypting the data does not come in the way of the effective and quick use of Zoho CRM, by authorized users.
Availability
Feature Specifications
Field and Module-based specifications
- Only Custom fields (both new and existing) can be encrypted. However, a field that is marked as unique cannot be encrypted directly. First, it must be unmarked as a unique field to enable encryption. Conversely, a field that is already encrypted cannot be set as unique until the encryption is removed. In summary, a field cannot be both unique and encrypted simultaneously. To switch between these states, you must first remove the existing designation.
- Fields that can be encrypted are Single Line, Email, Phone, Number, Multiline (small), Date, Date-Time, Currency, Decimal, Long Integer, and URL fields.
- Data encryption is available for all standard (except Tasks, Calls, and Meetings) and custom modules.
- Encryption can be disabled for a field at any time.
- In Lead Conversion Mapping, data can be converted and stored only between two encrypted fields.
- Encrypted fields can be used as inputs in Formula fields.
- Find & Merge and Deduplication are supported for encrypted fields.
- Any data imported to encrypted fields will be encrypted by default and exported data are decrypted.
- Encrypted fields can be included in Web forms.
- Encrypted field can be displayed in Reports as a column, but cannot be used in Criteria and Columns to Total.
- Encrypted fields can be used as inputs in custom functions, and as merge fields in templates.
- APIs are supported for encrypted data.
- Encrypted fields can be used in integrations too. Utilizing the information in integrations is entirely at the user's risk.
Limitations and Trade-offs
- Only full-text search is supported in global search. For instance, if the encrypted data is "Joseph Wells," the encrypted field record does not show in the results of a search for "Joseph."
- Encrypted fields cannot be used in Advanced Filters
- Encrypted fields cannot be found using Search by Criteria
- Encrypted fields are not visible in the Sort option.
- In the Forecasts module, encrypted fields cannot be used as Target Fields.
- When a field is encrypted, the following operators will be supported in the criteria:
- Single line, Phone, Email, Small multi-line (character limit of 2000), Date, Date-Time, and Currency - is empty and is not empty
- Number, Decimal, Long integer - =, !=, is empty, and is not empty.
File encryption: All the attachments are encrypted by default once added to CRM.
Email encryption: Emails sent and received via CRM will be encrypted at rest.
Read more about how data encryption takes place at Zoho. To encrypt/decrypt custom fields:
- Go to Setup > Customization > Modules and Fields > [Select the module] .
- In the module layout editor, go to the field you wish to encrypt, click the Settings icon and select Edit Properties.
- In the Field Properties popup, select the Encrypt Field checkbox.
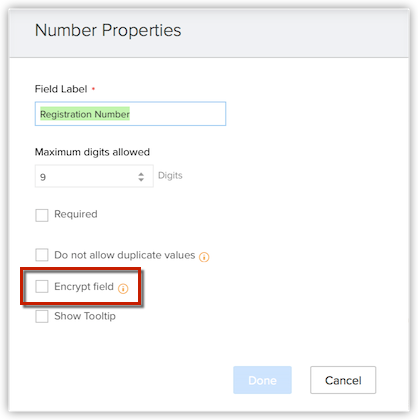
- Click Done.
- Save the layout.
Encryption Process at Zoho CRM
Encryption can be used in two situations.
- Encryption in Transit
- Encryption at Rest (EAR)
Encryption in Transit
Refers to data that is encrypted when it is in transit — including from your browser to the web server and other third parties via integrations.
Encrypting data in transit protects your data from man-in-the-middle attacks.
Read more.
Encryption at Rest
Refers to data that is encrypted when it is stored (not moving) — either on a disc, in a database, or some other form of media. In addition to encryption of data during transit, encryption of data when it is stored in the servers provides an even higher level of security. EAR protects against any possible data leak due to server compromise or unauthorized access.
Encryption is done at the application layer using the AES-256 algorithm which is a symmetric encryption algorithm and uses 128-bit blocks and 256-bit keys. The key used to convert the data from plain text to cypher text is called Data Encryption Key(DEK). The DEK is further encrypted using the KEK (Key Encryption Key),
thus, providing yet another layer of security. The keys are generated and maintained by our in-house Key Management Service (KMS).
Read more.
Full disk encryption is available at IN (India), AU (Australia), and JP (Japan) data centres and upon request we extend the facility to other DCs.
Read more.